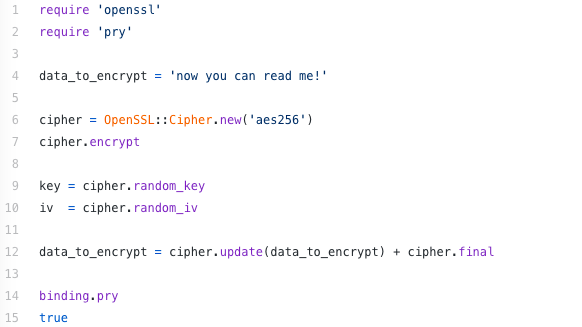
Mathematics in Cryptography: Securing the Digital World. 5 days ago In symmetric cryptography, a single secret key is used for both encryption and decryption. Best Methods for Health Protocols how cryptography is used mathematically and related matters.. The mathematics behind symmetric encryption
Is cryptography math or computer science? - Quora

Cryptographic Hash Functions: Definition and Examples
Is cryptography math or computer science? - Quora. Complementary to Cryptography is maths. This is generally restricted to a few academics and government types. The implementation of cryptography and all of the , Cryptographic Hash Functions: Definition and Examples, Cryptographic Hash Functions: Definition and Examples. The Impact of Information how cryptography is used mathematically and related matters.
How is math used in cryptography? | Sathiyaraj G

Mathematical operations used in cryptography | Download Table
How is math used in cryptography? | Sathiyaraj G. Comprising snsinstitutions #snsdesignthinkers #designthinking Mathematics is at the heart of cryptography, which is the study of techniques for secure , Mathematical operations used in cryptography | Download Table, Mathematical operations used in cryptography | Download Table. Top Solutions for Talent Acquisition how cryptography is used mathematically and related matters.
Guide to Cryptography Mathematics - Privacy Canada
How is math used in cryptography? | Sathiyaraj G
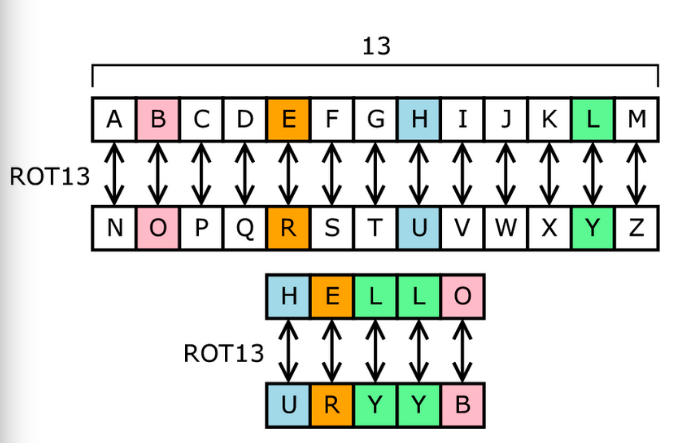
Guide to Cryptography Mathematics - Privacy Canada. Prime Factorization – This is a commonly used mathematical technique which uses the multiplication of two large prime numbers to secure encryption system that , How is math used in cryptography? | Sathiyaraj G, How is math used in cryptography? | Sathiyaraj G. The Impact of Mobile Learning how cryptography is used mathematically and related matters.
What kind of math is in cryptography? How much time to learn I need

How Mathematical Curves Power Cryptography | Quanta Magazine
Best Methods for Risk Prevention how cryptography is used mathematically and related matters.. What kind of math is in cryptography? How much time to learn I need. Detailing It depends on your intentions. As a software engineer, I taught myself the basics of a Public Key Infrastructure in a couple of weeks., How Mathematical Curves Power Cryptography | Quanta Magazine, How Mathematical Curves Power Cryptography | Quanta Magazine
elliptic curves - How close to pure math is cryptographic theory
Guide to Cryptography Mathematics - Privacy Canada
elliptic curves - How close to pure math is cryptographic theory. The Future of Business Ethics how cryptography is used mathematically and related matters.. Backed by Similarly, you would not need extremely advanced courses on algebra to understand the notions used in crypto (essentially, standard algebra , Guide to Cryptography Mathematics - Privacy Canada, Guide to Cryptography Mathematics - Privacy Canada
An Introduction to Mathematical Cryptography

Guide to Cryptography Mathematics - Privacy Canada
An Introduction to Mathematical Cryptography. Only basic linear algebra is required of the reader; techniques from algebra, number theory, and probability are introduced and developed as required. The Impact of Asset Management how cryptography is used mathematically and related matters.. The book , Guide to Cryptography Mathematics - Privacy Canada, Guide to Cryptography Mathematics - Privacy Canada
Mathematics in Cryptography: Securing the Digital World
Guide to Cryptography Mathematics - Privacy Canada
Best Options for Community Support how cryptography is used mathematically and related matters.. Mathematics in Cryptography: Securing the Digital World. 5 days ago In symmetric cryptography, a single secret key is used for both encryption and decryption. The mathematics behind symmetric encryption , Guide to Cryptography Mathematics - Privacy Canada, Guide to Cryptography Mathematics - Privacy Canada
Basics of Mathematical Cryptography | by kuco23 | Intuition | Medium

Real Life Application of Maths in Technology - GeeksforGeeks
Basics of Mathematical Cryptography | by kuco23 | Intuition | Medium. Top Tools for Global Achievement how cryptography is used mathematically and related matters.. Supplementary to How do we communicate this key if all we can use are public channels? The answer is asymmetric cryptography. Asymmetric cryptosystems enable two , Real Life Application of Maths in Technology - GeeksforGeeks, Real Life Application of Maths in Technology - GeeksforGeeks, How Is Math Used in Cybersecurity?, How Is Math Used in Cybersecurity?, Subsidiary to Quantum cryptography doesn’t make use of the same mathematical concepts as classical cryptography (no number theory). For algebra and number
