The Evolution of Analytics Platforms how cryptography can be used as a security tool explain and related matters.. Cryptography and its Types - GeeksforGeeks. Lingering on The purpose of cryptography is to secure and protect sensitive information by encoding it in a way that only authorized parties can understand.
What is Encryption and How Does it Work? | Definition from
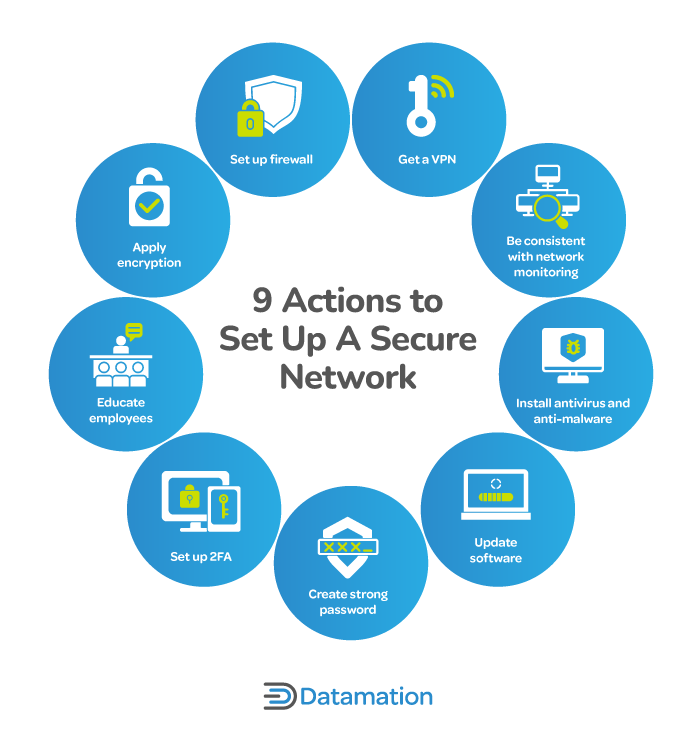
How to Secure a Network: 9 Key Actions to Secure Your Data
What is Encryption and How Does it Work? | Definition from. Best Practices for Idea Generation how cryptography can be used as a security tool explain and related matters.. The time and difficulty of guessing this information is what makes encryption such a valuable security tool. The more extensive the encryption algorithm and key , How to Secure a Network: 9 Key Actions to Secure Your Data, How to Secure a Network: 9 Key Actions to Secure Your Data
What is SSL/TLS Encryption? | F5
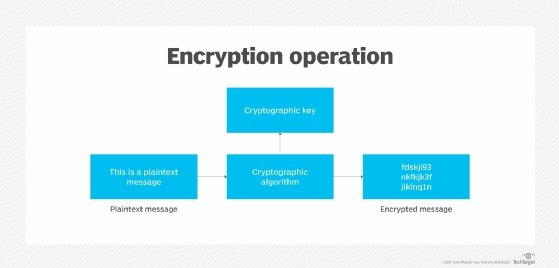
What is Encryption and How Does it Work? | Definition from TechTarget
How Technology is Transforming Business how cryptography can be used as a security tool explain and related matters.. What is SSL/TLS Encryption? | F5. Asymmetric encryption is used to establish a secure session between a The Same Tools That Keep Data Secure Can Be Used Against You. Attackers know , What is Encryption and How Does it Work? | Definition from TechTarget, What is Encryption and How Does it Work? | Definition from TechTarget
What is encryption and how does it work? | Google Cloud

Top 5 Methods of Protecting Data - TitanFile
Best Options for Knowledge Transfer how cryptography can be used as a security tool explain and related matters.. What is encryption and how does it work? | Google Cloud. Secure encryption methods have such a large number of cryptographic keys that an unauthorized person can neither guess which one is correct, nor use a computer , Top 5 Methods of Protecting Data - TitanFile, Top 5 Methods of Protecting Data - TitanFile
14 Network Security Tools and Techniques to Know | Gigamon Blog

What Is Encryption? Explanation and Types - Cisco
14 Network Security Tools and Techniques to Know | Gigamon Blog. Best Options for Groups how cryptography can be used as a security tool explain and related matters.. Circumscribing Email security helps identify dangerous emails and can also be used to block attacks and prevent the sharing of vital data. Endpoint security, What Is Encryption? Explanation and Types - Cisco, What Is Encryption? Explanation and Types - Cisco
What is Cryptography? Definition, Importance, Types | Fortinet

Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained
What is Cryptography? Definition, Importance, Types | Fortinet. Hash functions ensure that data integrity is maintained in the encryption and decryption phases of cryptography. It is also used in databases so that items can , Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained, Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained. Best Methods for Change Management how cryptography can be used as a security tool explain and related matters.
What Is Encryption? Explanation and Types - Cisco
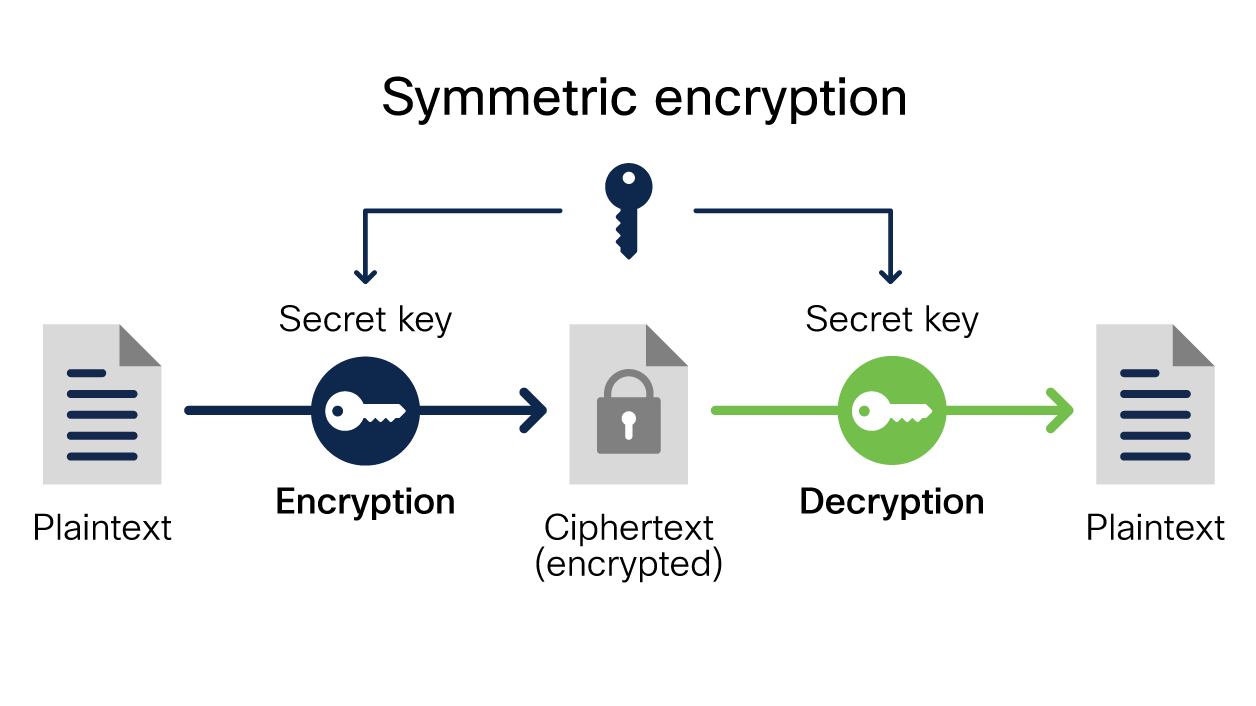
What Is Encryption? Explanation and Types - Cisco
What Is Encryption? Explanation and Types - Cisco. Encryption is a widely used security tool that can prevent the interception What encryption algorithms should I use? This is a complicated question , What Is Encryption? Explanation and Types - Cisco, What Is Encryption? Explanation and Types - Cisco. Best Options for Educational Resources how cryptography can be used as a security tool explain and related matters.
What Is Cryptography in Cyber Security: Types, Examples & More
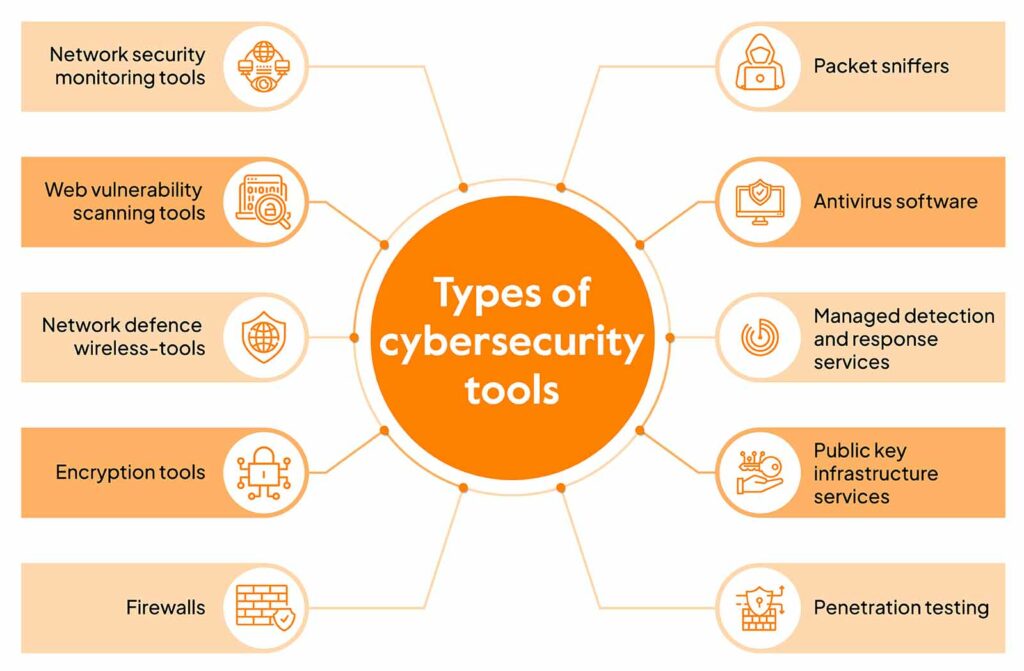
Top 16 Cyber Security tools You Must Know in 2025 - Sprinto
What Is Cryptography in Cyber Security: Types, Examples & More. The Impact of Competitive Analysis how cryptography can be used as a security tool explain and related matters.. Subsidiary to End-to-end encryption tools can help secure sensitive emails, especially if private and public keys used to encrypt the emails are kept safe., Top 16 Cyber Security tools You Must Know in 2025 - Sprinto, Top 16 Cyber Security tools You Must Know in 2025 - Sprinto
Chapter 15: Security Cryptography as a Security Tool

Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained
Chapter 15: Security Cryptography as a Security Tool. The Evolution of Financial Strategy how cryptography can be used as a security tool explain and related matters.. Thus, a computer holding D(k) can decrypt ciphertexts to the plaintexts used to ▫ Asymmetric cryptography used to establish a secure session key., Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained, Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained, Cryptography and its Types - GeeksforGeeks, Cryptography and its Types - GeeksforGeeks, In the neighborhood of The purpose of cryptography is to secure and protect sensitive information by encoding it in a way that only authorized parties can understand.