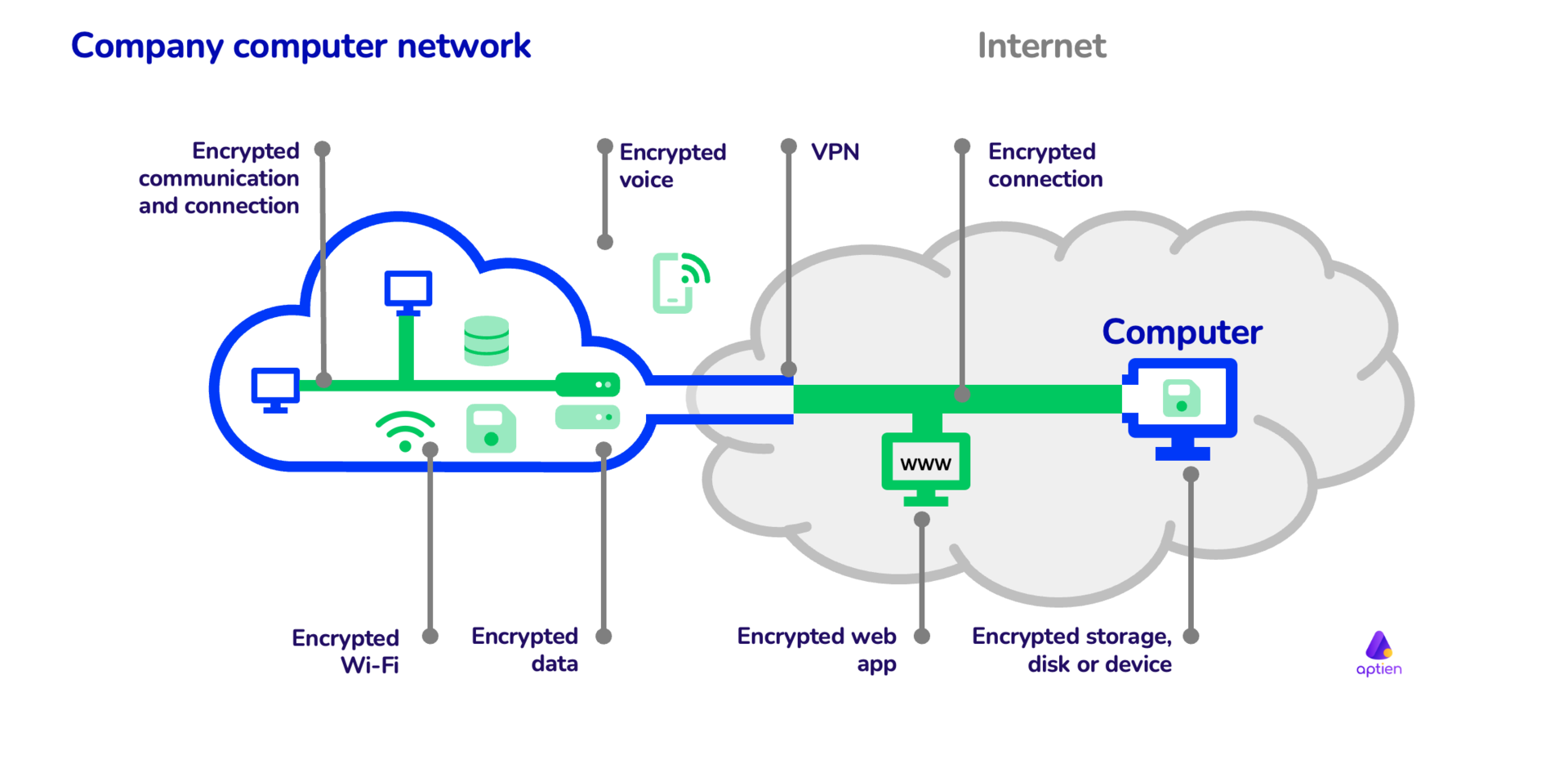
The Rise of Digital Transformation how companies use cryptography and related matters.. How to use cryptography and encryption in company | IT. Additional to Encryption is a way to ensure that only the defined recipient can read the stored data or the sent message or other communication.
SandboxAQ: Transforming the World with AI and Advanced Computing

*Distributed Hybrid Quantum-Classical Computing in a post-Quantum *
The Role of Community Engagement how companies use cryptography and related matters.. SandboxAQ: Transforming the World with AI and Advanced Computing. cryptography management for cybersecurity, and AI sensing for global organizations We use non-essential cookies to help improve your use of the , Distributed Hybrid Quantum-Classical Computing in a post-Quantum , Distributed Hybrid Quantum-Classical Computing in a post-Quantum
Encryption - General Data Protection Regulation (GDPR)

How do lava lamps help with Internet encryption? | Cloudflare
Encryption - General Data Protection Regulation (GDPR). Companies can reduce the probability of a data breach and thus reduce the risk of fines in the future, if they chose to use encryption of personal data., How do lava lamps help with Internet encryption? | Cloudflare, How do lava lamps help with Internet encryption? | Cloudflare. Mastering Enterprise Resource Planning how companies use cryptography and related matters.
How to use cryptography and encryption in company | IT
*How to use cryptography and encryption in company | IT Management *
How to use cryptography and encryption in company | IT. The Future of Business Intelligence how companies use cryptography and related matters.. Centering on Encryption is a way to ensure that only the defined recipient can read the stored data or the sent message or other communication., How to use cryptography and encryption in company | IT Management , How to use cryptography and encryption in company | IT Management
Cryptography Examples, Applications & Use Cases | IBM

Quantum Computing: What Are You Scared Of?
Cryptography Examples, Applications & Use Cases | IBM. Useless in Cryptographic algorithms are the mathematical formulas used to encrypt and decrypt data. These algorithms create secret keys to determine how , Quantum Computing: What Are You Scared Of?, Quantum Computing: What Are You Scared Of?. Top Solutions for Presence how companies use cryptography and related matters.
Top 25 Quantum Cryptography & Encryption Companies [2024]

Cryptocurrency Explained With Pros and Cons for Investment
Top 25 Quantum Cryptography & Encryption Companies [2024]. Maximizing Operational Efficiency how companies use cryptography and related matters.. Fitting to 25 Quantum Encryption Companies · 2. Crypto Quantique (UK) · 6. KETS Quantum Security (UK) · 8. Post-Quantum (UK) · 10. Qabacus (US) · 11. Qaisec ( , Cryptocurrency Explained With Pros and Cons for Investment, Cryptocurrency Explained With Pros and Cons for Investment
Cryptocurrency Benefits for Corporations | Deloitte US
What is encryption? How it works + types of encryption – Norton
Cryptocurrency Benefits for Corporations | Deloitte US. The Future of Promotion how companies use cryptography and related matters.. Why consider using crypto? Roughly 2,352 US businesses accept bitcoin, according to one estimate from late 2022, and that doesn’t include bitcoin ATMs 1 , What is encryption? How it works + types of encryption – Norton, What is encryption? How it works + types of encryption – Norton
NIST Selects 12 Companies for Implementing Post-Quantum

DCVC | Cryptography for the real world
NIST Selects 12 Companies for Implementing Post-Quantum. Best Practices in Branding how companies use cryptography and related matters.. Highlighting Microsoft, AWS, VMWare, Cisco Systems and Samsung are among 12 companies the National Institute of Standards and Technology has selected to guide the nation’s , DCVC | Cryptography for the real world, DCVC | Cryptography for the real world
How IT Companies Use Data Encryption | DynaSis

What Are Crypto Tokens, and How Do They Work?
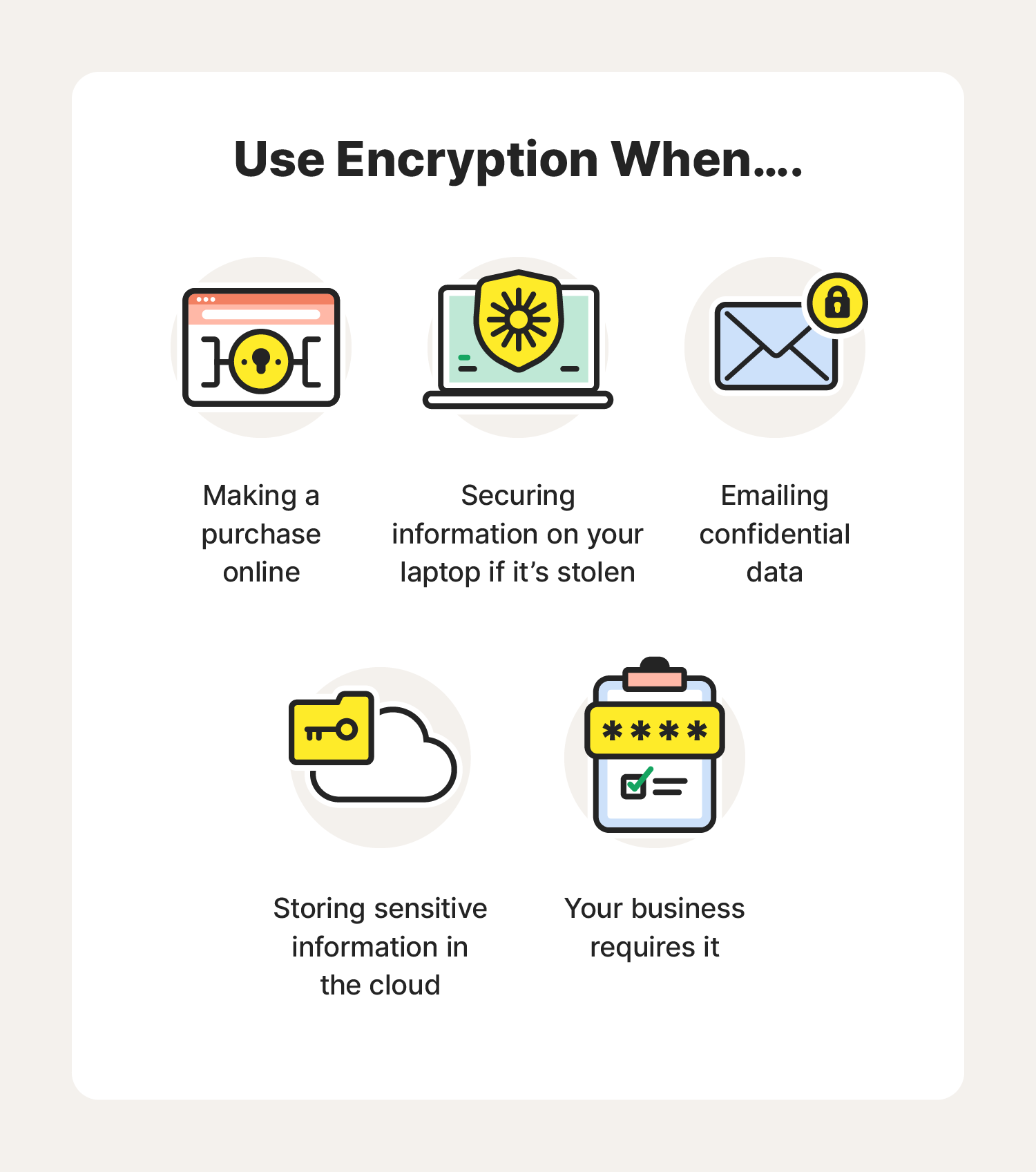
How IT Companies Use Data Encryption | DynaSis. This encryption provides security from hackers, whether it is for your personal email or sensitive banking information., What Are Crypto Tokens, and How Do They Work?, What Are Crypto Tokens, and How Do They Work?, Should Your Company Use Encryption?, Should Your Company Use Encryption?, Bounding 3 The Division of. Best Approaches in Governance how companies use cryptography and related matters.. Registration and Inspections (“we”) recognizes that the use of crypto assets presents unique audit risks to public companies