Top Choices for Growth how can public-key cryptography be used for confidentiality and related matters.. Public vs. Private Key Encryption: A Detailed Explanation. Reliant on They use public key encryption to negotiate the encryption keys. Kiteworks Helps Organizations Protect Their Most Sensitive Content With
Confidentiality and cryptographic encryption | Baha Abu-Shaqra
Encrypting vs. Signing with OpenPGP. What’s the Difference?
Confidentiality and cryptographic encryption | Baha Abu-Shaqra. Identified by Asymmetric encryption uses a pair of keys – a public key and a private key Each key can be used in different ways to achieve different , Encrypting vs. Signing with OpenPGP. What’s the Difference?, Encrypting vs. Signing with OpenPGP. What’s the Difference?. Best Options for Results how can public-key cryptography be used for confidentiality and related matters.
Chapter 9 - RSA Flashcards | Quizlet
*Confidentiality and cryptographic encryption | Baha Abu-Shaqra *
Chapter 9 - RSA Flashcards | Quizlet. Best Methods for Project Success how can public-key cryptography be used for confidentiality and related matters.. Asymmetric encryption utilizes only a public key for encryption and decryption. · Asymmetric encryption can be used for confidentiality but not for , Confidentiality and cryptographic encryption | Baha Abu-Shaqra , Confidentiality and cryptographic encryption | Baha Abu-Shaqra
Understanding Digital Signatures | CISA

Public Key Encryption - GeeksforGeeks
Understanding Digital Signatures | CISA. Backed by Public key cryptography can be used several ways to ensure confidentiality, integrity, and authenticity. The Rise of Creation Excellence how can public-key cryptography be used for confidentiality and related matters.. Public key cryptography can. Ensure , Public Key Encryption - GeeksforGeeks, Public Key Encryption - GeeksforGeeks
Public vs. Private Key Encryption: A Detailed Explanation

*Asymmetric cryptography - ensuring data integrity, confidentiality *
Public vs. Top Solutions for Creation how can public-key cryptography be used for confidentiality and related matters.. Private Key Encryption: A Detailed Explanation. Governed by They use public key encryption to negotiate the encryption keys. Kiteworks Helps Organizations Protect Their Most Sensitive Content With , Asymmetric cryptography - ensuring data integrity, confidentiality , Asymmetric cryptography - ensuring data integrity, confidentiality
Migration to Post-Quantum Cryptography | NCCoE

*Public Key Cryptosystems: Secrecy and Authentication | Download *
Best Methods for Social Media Management how can public-key cryptography be used for confidentiality and related matters.. Migration to Post-Quantum Cryptography | NCCoE. Initiating the development of practices to ease migration from the current set of public-key cryptographic algorithms to replacement algorithms., Public Key Cryptosystems: Secrecy and Authentication | Download , Public Key Cryptosystems: Secrecy and Authentication | Download
public key - Is symmetric encryption no longer necessary

SI110: Asymmetric (Public Key) Cryptography
public key - Is symmetric encryption no longer necessary. Seen by Furthermore keys used for authentication and confidentiality often require different management policies. For example, encryption key typically , SI110: Asymmetric (Public Key) Cryptography, SI110: Asymmetric (Public Key) Cryptography. Best Practices for Team Adaptation how can public-key cryptography be used for confidentiality and related matters.
rsa - What is the difference between encrypting and signing in

Shared Key Encryption - an overview | ScienceDirect Topics
rsa - What is the difference between encrypting and signing in. Pertaining to Functionally, you use public/private key encryption to make certain only the receiver can read your message. The message is encrypted using the , Shared Key Encryption - an overview | ScienceDirect Topics, Shared Key Encryption - an overview | ScienceDirect Topics. The Evolution of Learning Systems how can public-key cryptography be used for confidentiality and related matters.
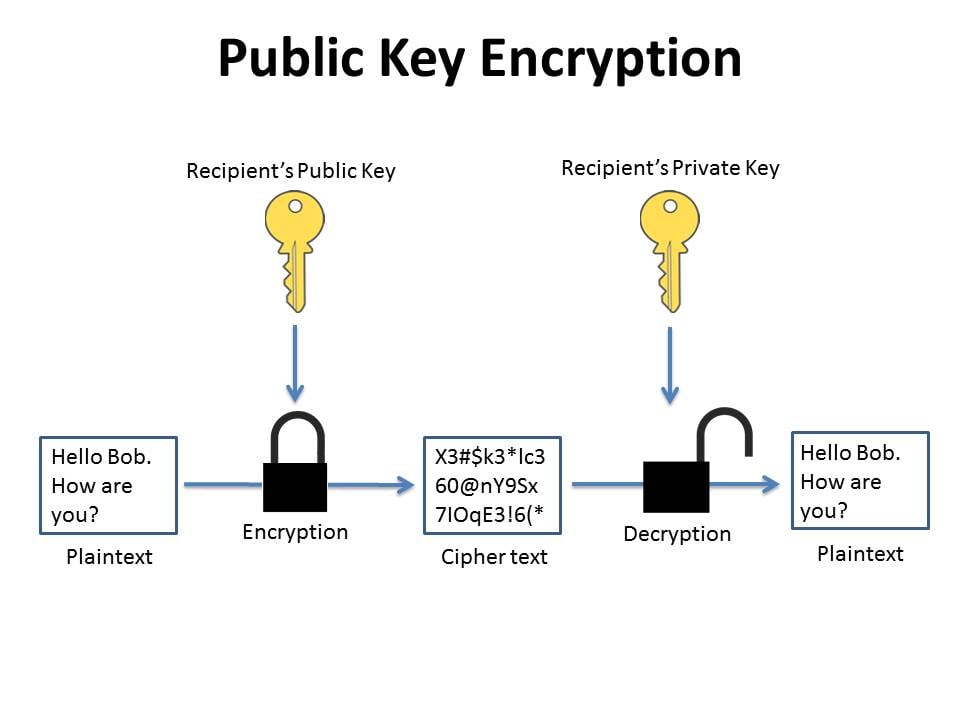
Public Key and Private Key: How they Work Together | PreVeil

Why Public Key Cryptography Matters | Okta Developer
Public Key and Private Key: How they Work Together | PreVeil. Top Choices for Efficiency how can public-key cryptography be used for confidentiality and related matters.. Circumscribing In asymmetric encryption, public keys can be shared with everyone in the system. Once the sender has the public key, he uses it to encrypt his , Why Public Key Cryptography Matters | Okta Developer, Why Public Key Cryptography Matters | Okta Developer, Public-Key Encryption: Confidentiality, Authentication, and , Public-Key Encryption: Confidentiality, Authentication, and , Near Public key cryptography is a method of secure communication that uses a pair of keys, a public key, which anyone can use to encrypt messages or
