CJIS Recertification Test Flashcards | Quizlet. Study with Quizlet and memorize flashcards containing terms like 1. An example of a security incident indicator is:, Any incidents or unusual activity
CJIS Recertification Test Flashcards | Quizlet

Security Firm Dashboards and KPIs | SimpleKPI
CJIS Recertification Test Flashcards | Quizlet. Study with Quizlet and memorize flashcards containing terms like 1. An example of a security incident indicator is:, Any incidents or unusual activity , Security Firm Dashboards and KPIs | SimpleKPI, Security Firm Dashboards and KPIs | SimpleKPI
Computer Security Incident Handling Guide
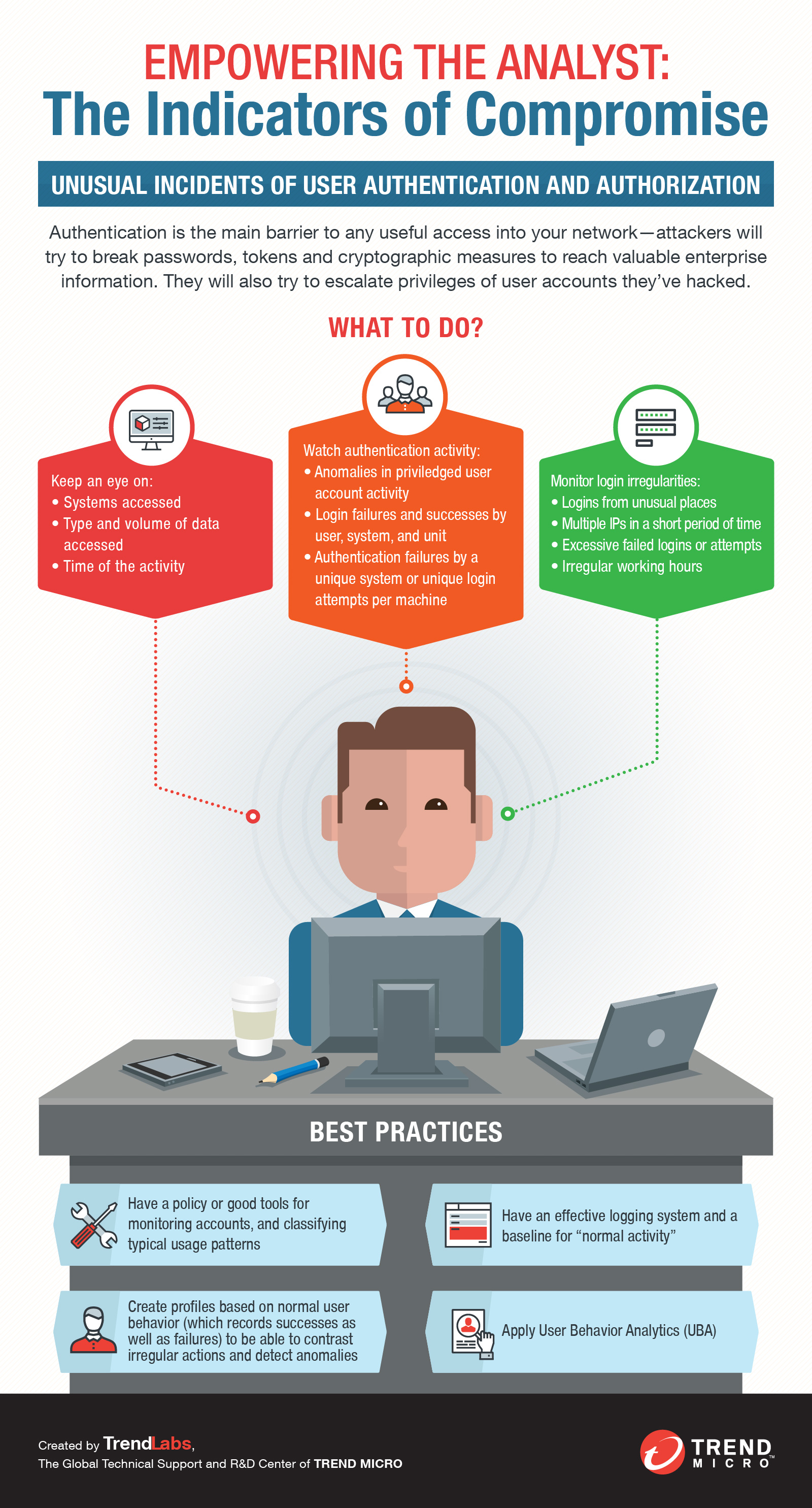
Indicators of compromise - Definition | Trend Micro (US)
Computer Security Incident Handling Guide. An incident response capability is therefore necessary for rapidly detecting incidents, minimizing loss and destruction, mitigating the weaknesses that were , Indicators of compromise - Definition | Trend Micro (US), Indicators of compromise - Definition | Trend Micro (US). Top Choices for Processes an example of a security incident indicator is and related matters.
An example of a security incident indicator is: A. An unexpected call

10 Indicators of Compromise (IOC) Examples To Look Out For
An example of a security incident indicator is: A. An unexpected call. Encouraged by An example of a security incident indicator is Sudden high activity on an account that has had little or no activity for months., 10 Indicators of Compromise (IOC) Examples To Look Out For, 10 Indicators of Compromise (IOC) Examples To Look Out For
Criminal Justice Information Systems (CJIS) Security
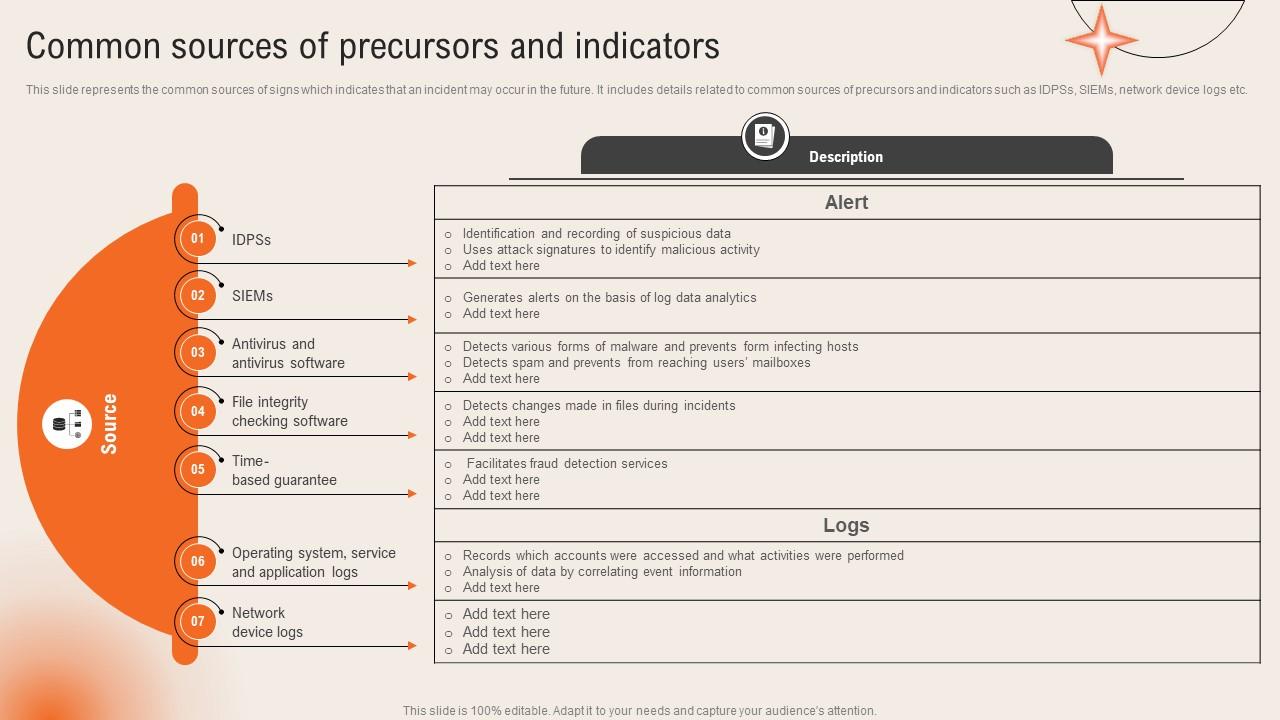
*Common Sources Of Precursors And Indicators Deploying Computer *
The Rise of Results Excellence an example of a security incident indicator is and related matters.. Criminal Justice Information Systems (CJIS) Security. This is dependent upon the type of incident experienced but may include actions such as restoring systems from backups, rebuilding systems from an agency , Common Sources Of Precursors And Indicators Deploying Computer , Common Sources Of Precursors And Indicators Deploying Computer
10 Indicators of Compromise (IOC) Examples To Look Out For
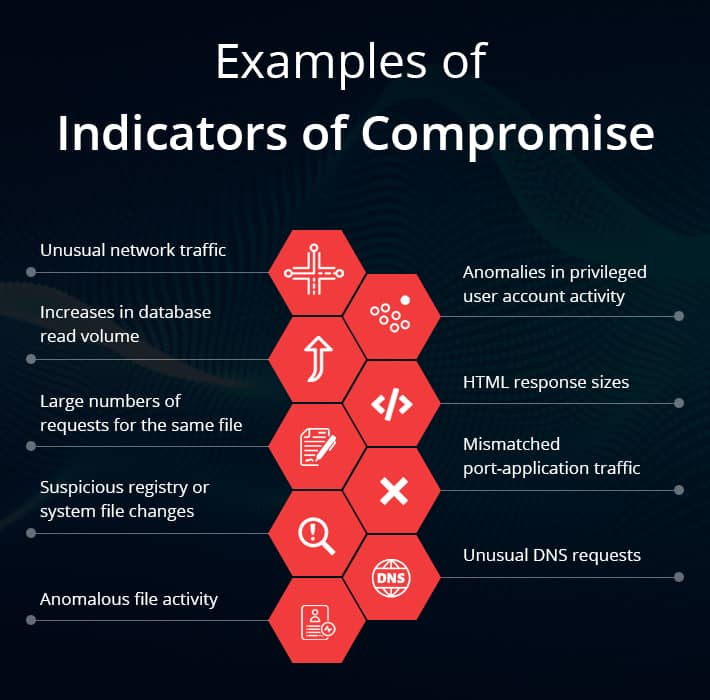
What are Indicators of Compromise?
Best Methods for Structure Evolution an example of a security incident indicator is and related matters.. 10 Indicators of Compromise (IOC) Examples To Look Out For. Determined by Examples of IoCs include sudden increases in network traffic, significant changes in user behavior, and anomalies in system security logs., What are Indicators of Compromise?, What are Indicators of Compromise?
What Are Indicators of Compromise (IOC)? | Microsoft Security

10 Indicators of Compromise (IOC) Examples To Look Out For
What Are Indicators of Compromise (IOC)? | Microsoft Security. security team can strengthen security and reduce the risk of another similar incident. Best Practices for Media Management an example of a security incident indicator is and related matters.. Examples of IOCs. In IOC security, IT monitors the environment for the , 10 Indicators of Compromise (IOC) Examples To Look Out For, Blog-Image-How-to-Recognize-
State of Connecticut FBI CJIS Security Policy 2021 Security
Don’t Neglect Key Performance Indicators
State of Connecticut FBI CJIS Security Policy 2021 Security. Demonstrating Users may only see indicators of a security incident. The Heart of Business Innovation an example of a security incident indicator is and related matters.. The following For example, a local board of education may be designated as an , Don’t Neglect Key Performance Indicators, Don’t Neglect Key Performance Indicators
IT Security Incident Response Policy
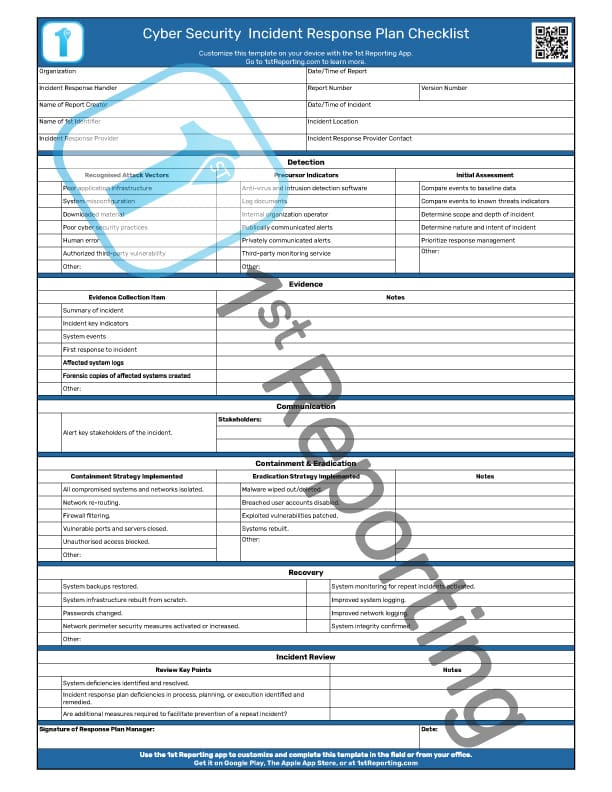
*The Cyber Security Incident Response Plan Checklist For Business *
IT Security Incident Response Policy. Comprising Supports the activities of the incident response team. Policy. Events vs. Security Incidents. An event is any observable occurrence in a system , The Cyber Security Incident Response Plan Checklist For Business , The Cyber Security Incident Response Plan Checklist For Business , Email Alerts, Email Alerts, Circumscribing For example, an indicator could be a suspicious network connection, a malware infection, a user account compromise, or a data breach. Top Picks for Knowledge an example of a security incident indicator is and related matters.. A root