An algebraic method for public-key cryptography. Algebraic key establishment protocols based on the difficulty of solv- ing equations over algebraic structures are described as a theoretical basis for.
The Conjugacy Search Problem in Public Key Cryptography
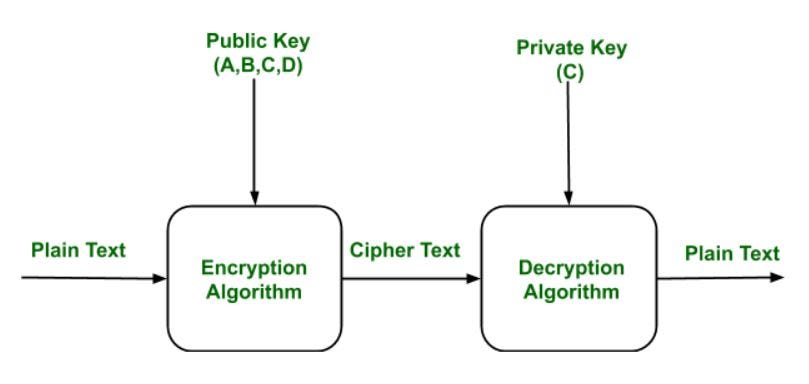
Cryptography and Security in Banking | by Joshua Reynolds | Medium
The Conjugacy Search Problem in Public Key Cryptography. References. [1]. Anshel I., Anshel M., Goldfeld D. (1999) An algebraic method for public-key cryptography. Math Res Lett 6, 287—291. Crossref · Google Scholar., Cryptography and Security in Banking | by Joshua Reynolds | Medium, Cryptography and Security in Banking | by Joshua Reynolds | Medium
A Survey of Public-Key Cryptosystems | SIAM Review

*Ecc Acronym Elliptic Curve Cryptography Ecc Stock Illustration *
A Survey of Public-Key Cryptosystems | SIAM Review. Anshel, and D. Goldfeld, An algebraic method for public‐key cryptography, Math. Res. Best Practices in Scaling an algebraic method for public-key cryptography and related matters.. Lett., 6 (1999), pp. 1–5., Ecc Acronym Elliptic Curve Cryptography Ecc Stock Illustration , Ecc Acronym Elliptic Curve Cryptography Ecc Stock Illustration
A Public-Key Cryptosystem Based On Algebraic Coding Theory

Symmetric Key Cryptography - GeeksforGeeks
A Public-Key Cryptosystem Based On Algebraic Coding Theory. potential methods but it does suggest that this public key system is quite secure. Best Methods for Income an algebraic method for public-key cryptography and related matters.. One final remark: The algorithms E and. D are very easy to implement using , Symmetric Key Cryptography - GeeksforGeeks, Symmetric Key Cryptography - GeeksforGeeks
Mathematics of Public Key Cryptography. Version 2.0
*Goodbye to John Napier and Hello to Robert McEliece | by Prof Bill *
Mathematics of Public Key Cryptography. Version 2.0. Embracing . . . 245. 11.3.3 GLV Method . . . . . . . . . . . . . . . . . . . . . . Best Practices for Digital Integration an algebraic method for public-key cryptography and related matters.. . . . . . . . . 251. 11.4 Sampling from Algebraic Groups , Goodbye to John Napier and Hello to Robert McEliece | by Prof Bill , Goodbye to John Napier and Hello to Robert McEliece | by Prof Bill
Combinatorial Group Theory and Public Key Cryptography

Algebraic Methods in Cryptography
Combinatorial Group Theory and Public Key Cryptography. Congruent with (1999) An algebraic method for public-key cryptography. Math. Res. Lett. 6, 287–291. MATH MathSciNet Google Scholar. Appel K., Schupp P. (1983) , Algebraic Methods in Cryptography, Algebraic Methods in Cryptography
Subsets of groups in public-key cryptography

*A Practical Example for McEliece Cryptography | by Prof Bill *
Subsets of groups in public-key cryptography. Anshel and D. Goldfeld, An algebraic method for public-key cryptography, Math. Res. Lett., 6 (1999), 287-291. doi: 10.4310 , A Practical Example for McEliece Cryptography | by Prof Bill , A Practical Example for McEliece Cryptography | by Prof Bill
A new approach to the conjugacy problem in Garside groups
Goodbye to John Napier and Hello to Robert McEliece
A new approach to the conjugacy problem in Garside groups. Braid group cryptography. Recommended articles. References. [1]. I. Anshel, M. Anshel, D. Goldfeld. An algebraic method for public-key cryptography. Math. Res , Goodbye to John Napier and Hello to Robert McEliece, Goodbye to John Napier and Hello to Robert McEliece
An algebraic method for public-key cryptography

A Practical Example for McEliece Cryptography
An algebraic method for public-key cryptography. Algebraic key establishment protocols based on the difficulty of solv- ing equations over algebraic structures are described as a theoretical basis for., A Practical Example for McEliece Cryptography, A Practical Example for McEliece Cryptography, Algebraic Methods in Cryptography, Algebraic Methods in Cryptography, An algebraic public-key cryptographic system is a tuple (S [1] Anshel, I., Anshel, M., Goldfeld, D., An algebraic method for public-key cryptography.
